In this project I developed and managed a Security Operations Center (SOC) in a home business lab, deploying a custom SIEM for real-time monitoring and alert generation, and integrated a Threat Intelligence feed using Azure.
Setting Up the Virtual Machine in Azure:
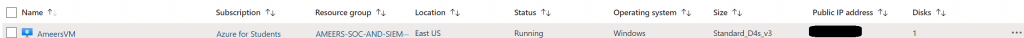
Creating the Virtual Machine (VM) was straightforward, thanks to Azure’s option for using a VM with preset configurations. I started by creating a Resource Group named AMEERS-SOC-AND-SIEM-PROJECT and then assigned a name to my VM. I chose Windows 11 Pro as the VM image and configured the username and password.
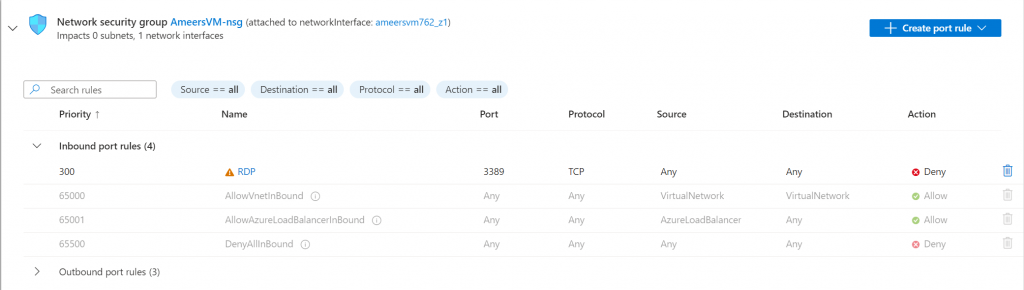
To ensure proper access, I selected “Allow selected ports” in the port rules and chose RDP (3389) as the inbound port to enable immediate traffic. After that, I proceeded with the default VM setup and successfully created the VM.
Create/Adding Microsoft Sentinel to workspace:
After accessing Microsoft Sentinel, I selected the option to add a new Microsoft Sentinel instance to my workspace and chose the Resource Group AMEERS-SOC-AND-SIEM-PROJECT that I had created earlier. I named the new instance Ameers-LogAnalytics.
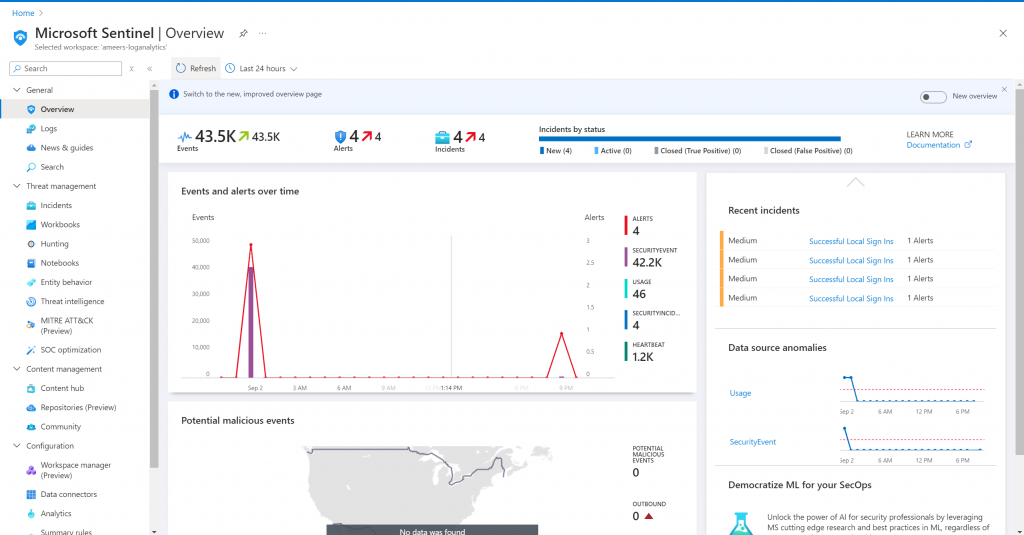
I than integrated this instance with my Virtual Machine (VM). I have to say Microsoft Sentinel proved to be quite engaging. The graphical user interface (GUI) and the dynamic statistics it presented were both cool and informative. The visualizations and data insights provided by Sentinel offered a deeper understanding of my VM’s security and the effectiveness of the monitoring setup.

Integrating VM Event Logs into Log Analytics and Sentinel Workspaces:
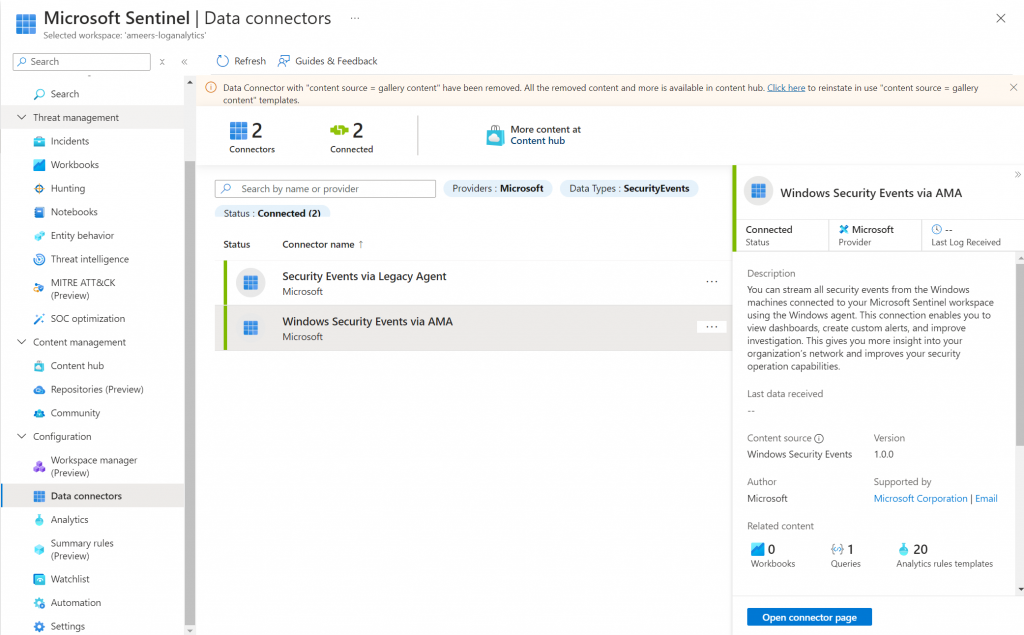
I returned to the Microsoft Sentinel page and navigated to the Data Connectors tab. From there, I accessed the Content Hub to install the Windows Security Events connector. During the installation process, I encountered two available versions of the connector.
After researching and using my brain the legacy agent is being phased out, I opted for the newer version that utilizes Azure Monitor Agent (AMA). This decision ensures compatibility and continued support, which helps with the the effectiveness of the data collection for Windows Security Events.
I then created a new Data Collection Rule named “WindowsEventstoSentinel.” In the Resources tab, I specified that the data should be pulled from the Virtual Machine (VM) that we set up earlier.
In the Collection tab, I selected all security events to ensure comprehensive data capture. With the configuration complete, I finalized the setup, and the rule was successfully created. This process enabled seamless integration of security event data from the VM into Microsoft Sentinel, giving me monitoring and analysis.
Creating Sentinal Rule:
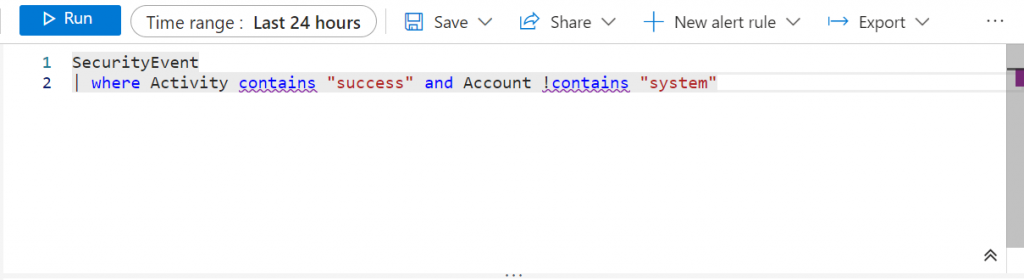
To monitor for successful Remote Desktop Protocol (RDP) sign-ins, which could indicate potential brute force attacks, I made a rule using Kusto Query Language (KQL). Given a little knowledge/background in SQL, I found that many concepts translated well to KQL, making the learning process smoother.
I explored and experimented with KQL to develop a query that shows successful RDP sign-ins. This involved filtering the logs to capture activities where users successfully signed in via RDP, providing valuable insights into potential security threats.
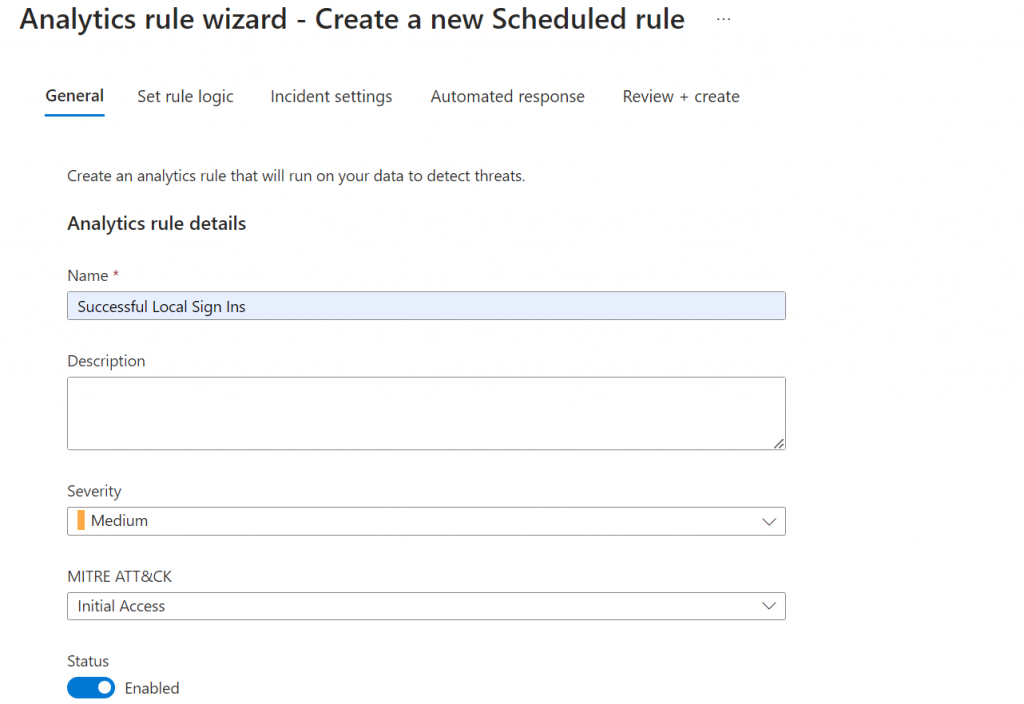
After developing the KQL query to detect successful RDP sign-ins, I proceeded to configure the rule settings. I set the Severity level to Medium, although, in this case, any severity level would have been fine given the context of the detection.
For the MITRE ATT&CK framework, I chose Initial Access, as successful RDP sign-ins align with the initial access tactics described. This categorization helps in correlating the detected events with known attack techniques and enhances the rule’s effectiveness in identifying potential threats.
Next, I configured the rule logic by setting the query scheduling to run every 5 minutes. This frequency ensures that the query continuously monitors for relevant events and provides real-time detection.
To capture recent activity, I set the data lookup to cover the last 5 minutes. This configuration allows the rule to detect and respond to potential threats promptly.
Additionally, I adjusted the alert threshold to trigger an alert for any query result greater than 0. This setting makes sure that even a single instance of the specified condition will generate an alert, enhancing the responsiveness of the detection mechanism.
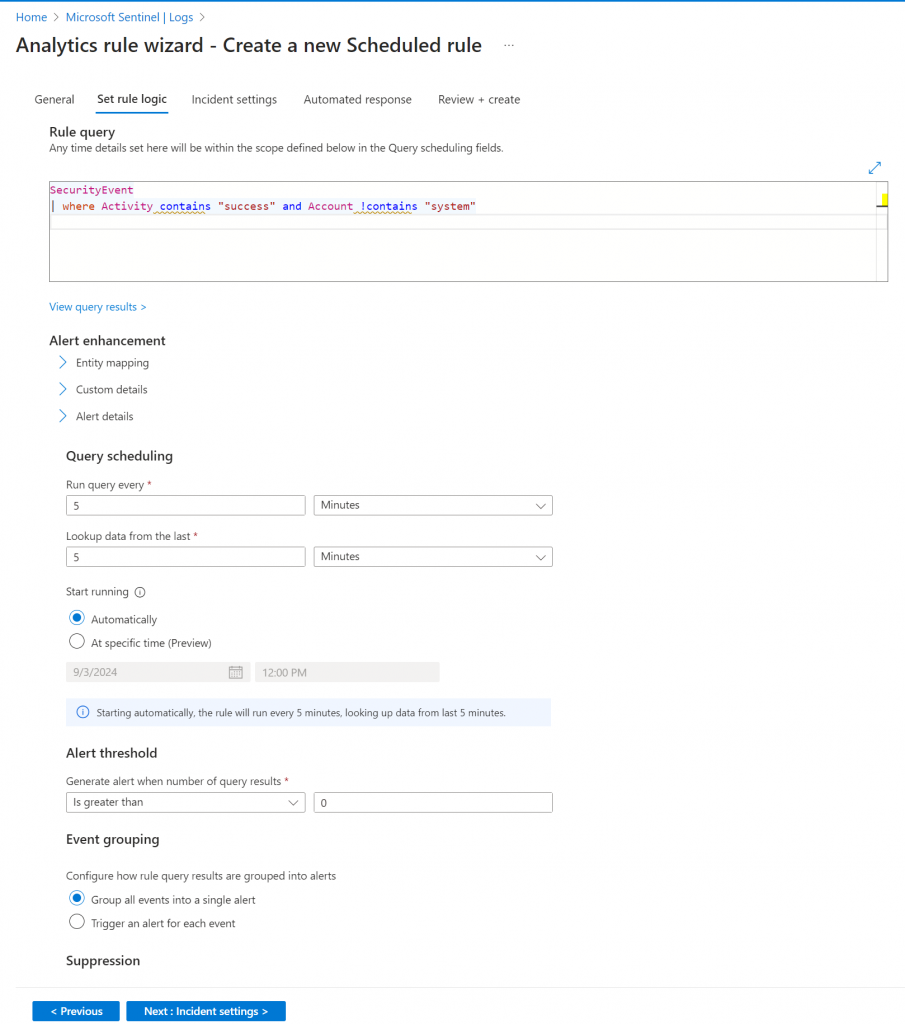
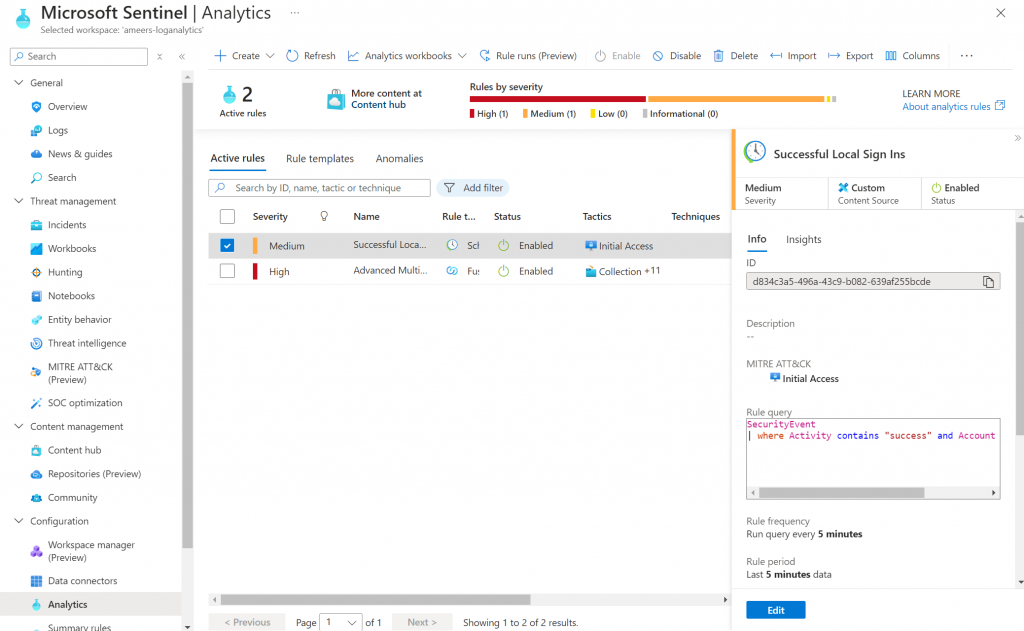
Now in the rules page I see the rule that I created about Succesful sign-ins.
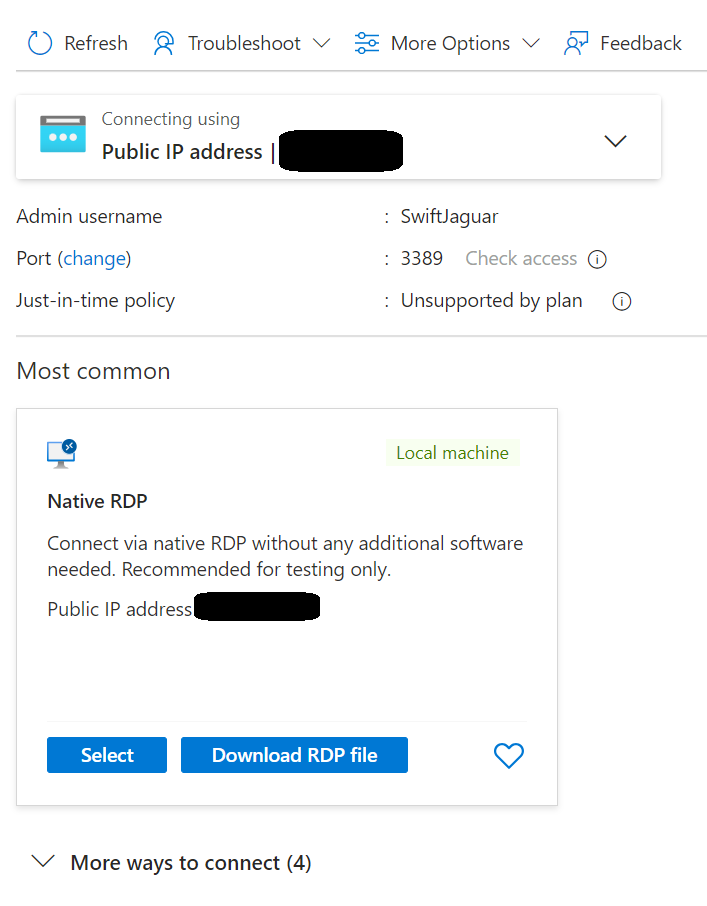
Testing:
To test the alerting functionality of my system, I first connected to the VM using Native RDP. I logged in with my username and password and then closed the VM to check if any alerts were generated. After waiting for 5 minutes, I received the expected alert, confirming that the system was correctly identifying and reporting successful logins.
Due to it working, I decided to conduct another test. I logged in again and confirmed that the alerting system triggered as expected. This validated that the system effectively monitors and alerts on login events, showing where and who accessed the VM.
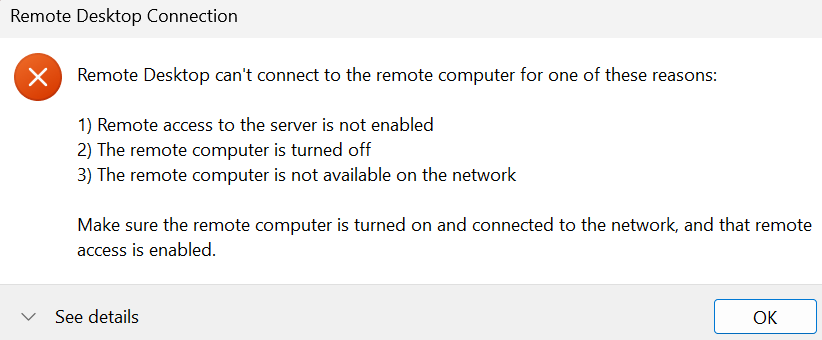
Next, I wanted to see how the system would behave with restricted access. I closed the RDP port and attempted to log in again. This time, I encountered an error indicating that the VM was blocking the connection and suggested trying a different connection method. This test demonstrated that the system correctly handles scenarios where the RDP port is closed, further confirming the hardness of the alerting and access control setup.
Conclusion:
This project provided a comprehensive hands-on experience in setting up and managing a Security Operations Center (SOC) within a home business lab environment. By deploying a custom SIEM and integrating it with Microsoft Sentinel, I was able to create a monitoring system capable of real-time alert generation and threat detection. The successful implementation of security event logging, RDP sign-in monitoring, and alert configuration showed the effectiveness of the system in identifying and responding to potential threats. Through testing and refining the setup, I gained valuable insights into the practical application of SOC principles and the importance of continuous monitoring and proactive security measures. This project not only enhanced my technical skills but also reinforced my understanding of cybersecurity practices critical to protecting organizational assets in a real-world scenario.
Getting hands-on experience with projects like this, even in a home lab setting, is incredibly exciting for me. It gives me that passion for learning and makes me want to apply these skills in a professional environment. There’s so much potential to build upon what I’ve created here, and I’m looking forward to expanding this project further,. I’ve also though about doing a project like setting up a Honeypot lab. I’ll need to do more research and find some walkthroughs, just as I did with this project, to guide me through the process.
When I first started reading about how to approach projects, I mistakenly believed that watching tutorials, seeking help, or following step-by-step guides was basically “cheating” myself. However, my perspective has completely shifted. I now understand that true learning comes from collaboration and using available resources. It’s not about finishing a project with the same level of knowledge you started with; it’s about growing and deepening your understanding throughout the process.
For me, this project, being one of my first major technical trials, highlighted the value of collaboration in the cybersecurity field. By working through challenges with the help of others and utilizing available resources, I’ve learned far more than I could have on my own. In the end, the goal is to know more today than I did yesterday, and that’s what makes this journey so rewarding.
References:
A big shout-out to Mad Hat, one of my favorite YouTubers in the cybersecurity space. His ability to break down complex concepts and make them accessible is CRAZY! His comment section is also a goldmine of additional insights, with Q&As that help along the way.
I’m really hoping he dives into Honeypots next and perhaps even creates a comprehensive Honeypot lab or project. As I mentioned earlier, I’m eager to get my hands dirty with Honeypots—quite literally, I want to get some honey on my fingers!
